Authentication
OIDC Authentication
VNS3 Licensing
Access Management
Clientpack Generation
Installing HTTPS
Firewall 2.0
Firewall
AWS Specific features
Firewall FWSets
VNS3 Variables
VNS3 Router
IPsec Configuration
IPsec Parameters
VNS3 Peering Mesh
Setting Topology Name
VNS3 Overlay Network
Snapshot Management
VNS3 Event Alerting
Network Address Translation
Traffic inspection
SNMP Support
VNS3 BGP Configuration Guide
Remote Support
Resetting VNS3
Upgrading
VNS3 Release Notes
VNS3 EOL Policy and Milestones
IPSec Connection Checklist
VNS3 Known Issues
VNS3 Specifications
VNS3 VPN Client tools
VNS3 Control Center
VNS3 setup
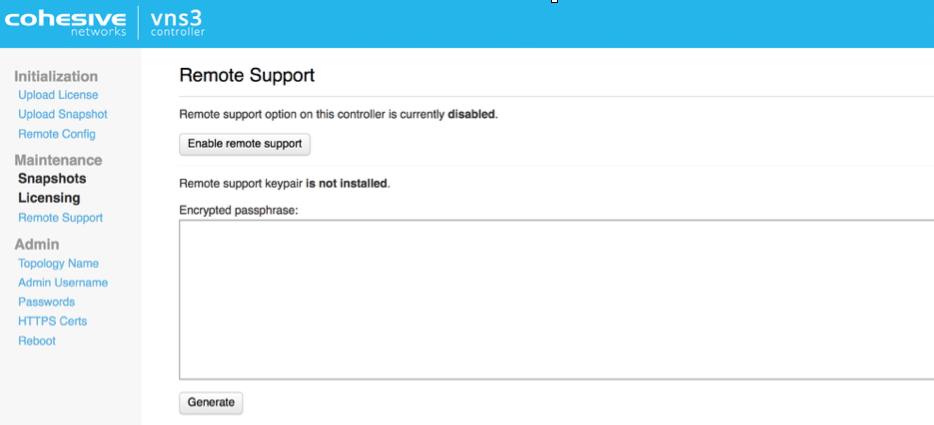
Remote Support
Overview
In the event Cohesive needs to observe runtime state of a VNS3 Controller in response to a tech support request, we will ask you to open Security Group access to TCP port 22 (SSH) from our support IP, 54.236.197.84, and Enable Remote Support via the Web UI.
Firewall
Note that TCP 22 (ssh) is not required for normal operations.
Secure, temporary access
Each VNS3 Controller is running a restricted SSH daemon, with access limited only to Cohesive for debugging purposes controlled by the user via the Remote Support toggle and key exchange generation.
Cohesive Networks will send you an encrypted passphrase to generate a private key used by Cohesive Support staff to access your Controller. Access to the restricted SSH daemon is completely controlled by the user. Once the support ticket has been closed you can disable remote support access and invalidate the access key. This two step process enables you to revoke access at any time and ensure that no third party can every gain access to VNS3 controllers.
Get in touch with support here.
VNS3 has NO secret passwords!
Updated on 24 Apr 2020
