Authentication
OIDC Authentication
VNS3 Licensing
Access Management
Clientpack Generation
Installing HTTPS
Firewall 2.0
Firewall
AWS Specific features
Firewall FWSets
VNS3 Variables
VNS3 Router
IPsec Configuration
IPsec Parameters
VNS3 Peering Mesh
Setting Topology Name
VNS3 Overlay Network
Snapshot Management
VNS3 Event Alerting
Network Address Translation
Traffic inspection
SNMP Support
VNS3 BGP Configuration Guide
Remote Support
Resetting VNS3
Upgrading
VNS3 Release Notes
VNS3 EOL Policy and Milestones
IPSec Connection Checklist
VNS3 Known Issues
VNS3 Specifications
VNS3 VPN Client tools
VNS3 Control Center
VNS3 setupVNS3 Peering Mesh
Overview
Controllers connect to each other in a process called Peering. Peered Controllers create a redundant, highly available and secure overlay network and share traffic load from the overlay network connected servers. A VNS3 mesh network of peered controllers will automatically handle re-routing of traffic in the case of failover.
Peering requires the following firewall rules:
UDP 1195-1203 - For tunnels between Controller peers; must be accessible from all peers in a given topology.
Configuring Peering
VNS3 controller peering involves the following steps for each controller in a topology:
- Set controller peer ID
- Provide the address and ID for each other peer in the mesh
Configuring via UI
- From the menu on the left, click Controller Peering under Overlay.
- Select “this instance” for this controller’s ID
- For each peer controller in the mesh, add the controller’s address for each ID. The address can be any resolvable and routable address (IP or DNS)
- Save changes
The Peering Setup Page will display the number of Controllers allowed to peer together in your topology as defined by the license file used to configure the Controller.For Controller #1 select “this instance” from drop down, instead of specifying its IP. To be valid, your form must have “this instance” value in one and only one drop-down.

If your topology has unused Controllers, leave the extra fields set to “not set”. If you have a multiple Controller topology, enter the Public DNS address of the second Controller for Controller #2. Repeat this for each additional Controller in your topology.
NOTE: Firewall rules added to a specific controller are not automatically synced to other controllers in the peered mesh.
Configuring via API
- PUT self peering ID
- POST peers for each peer
Each step must be taken for each controller in the mesh
Peering controller 2: Fetching Topology Configuration from Controller 1
In multiple controller topology, you much fetch the topology configuration from the initial controller licensed
UI
- Log in to the second VNS3 Controller UI.
- Click Fetch Keyset as keys must be generated only once per topology
- Type in private IP address of Controller #1 (where keys were generated) and the security token used to generate the keys on Controller #1. This will start a fetch process that will copy the clientpack cryptographic keys to the second Controller.
API
- Issue PUT /keyset request with the
sourceandtokenparameters where source=IP address of controller 1 - Repeat #1 for each peer in the mesh
Peering Controller 2: Set Peering
Setting peering for controller 2 is the same as controller 1:
- Set controller 2’s ID as 2 by selecting “this instance” for ID 2.
- Set controller 2’s peers for each other controller in the mesh
For Controller #2 select “this instance” from drop down, instead of specifying its IP. To be valid, your form must have “this instance” value in one and only one dropdown.
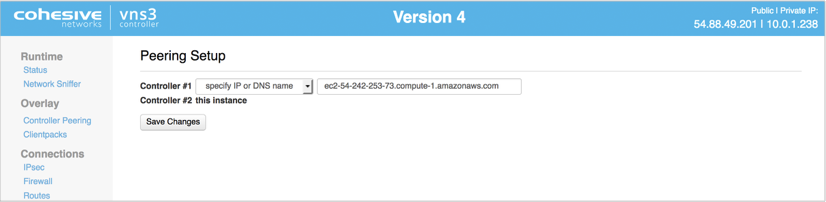
When done select Save Changes.
You should then get a status p age showing that this Controller was able to reach the other launched Controller instances. Go to Status page to verify that topology checksum on Controller #1 corresponds to that of Controller #2.
View Peering Status
The Runtime Status page displays a summary of all runtime configuration information.

- Controller Status The Controller’s identity within the Overlay Network (which was setup in the Peering steps) is displayed in this section.
- Peers and Clients Connections to other Controllers (called Peers) and client servers (called clients) are displayed in this section. If you setup a multiple Controller topology in the Peering steps you will see a Peered Controller listed. If you setup a single Controller topology, you will see no Peers.
- System Status Instance level information is displayed in this section.
The VNS3 Controller is ready for connections to be added. We recommend starting with configuring any IPsec connections that are needed before connecting client servers via clientpacks.
Updated on 16 Aug 2019
