Authentication
OIDC Authentication
VNS3 Licensing
Access Management
Clientpack Generation
Installing HTTPS
Firewall 2.0
Firewall
AWS Specific features
Firewall FWSets
VNS3 Variables
VNS3 Router
IPsec Configuration
IPsec Parameters
VNS3 Peering Mesh
Setting Topology Name
VNS3 Overlay Network
Snapshot Management
VNS3 Event Alerting
Network Address Translation
Traffic inspection
SNMP Support
VNS3 BGP Configuration Guide
Remote Support
Resetting VNS3
Upgrading
VNS3 Release Notes
VNS3 EOL Policy and Milestones
IPSec Connection Checklist
VNS3 Known Issues
VNS3 Specifications
VNS3 VPN Client tools
VNS3 Control Center
VNS3 setup
Traffic inspection
Overview
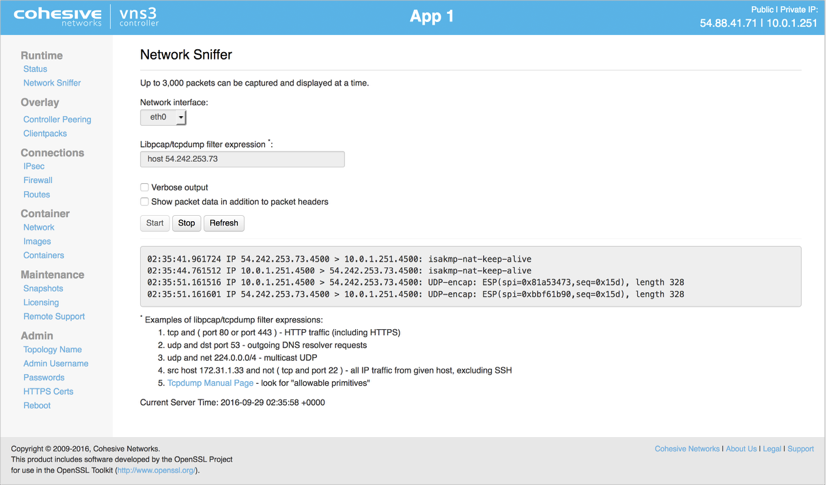
The Network Sniffer is a great troubleshooting tool. You can monitor most interfaces, including the “underlay” interfaces ethX, the overlay interface tun0, and VPN interfaces such as greX and ipsec_vtiX.
The Network Sniffer page includes some basic guidance regarding syntax. In the event your filter expression is malformed, the page will result in an “expression syntax error”.
Linux tcpdump/libpcap Expressions
The Network Sniffer accepts Linux tcpdump/libpcap filter expressions. Almost all qualifiers supported by libpcap are supported by VNS3. For more information, read the official libpcap filter documentation or reach out to our support team at support.cohesive.net or by email at support@cohesive.net.
When using the Network Sniffer, there are two things to remember:
- The page does not auto refresh. Once you click Start, be sure to click the refresh button to update your view of the traffic.
- The interface selection is very important.
- eth0 - Default network interface. This is where encapsulated IPsec traffic and unencrypted VLAN traffic is visible.
- tun0 - Overlay Network interface
- greX - GRE VPN virtual interface
- ipsec_vtiX - VTI VPN virtual interface

Troubleshooting
It is useful in troubleshooting an encrypted tunnel to first see if there is normal negotiation and keepalive traffic moving between the two IPsec Peers. This will help you to understand if there is a network connectivity or a firewall issue that prevents the negotiation.
Once a tunnel is negotiated, you can use the Network Sniffer to monitor tunnel traffic, making sure encrypted/encapsulated packets are moving in both directions.
Use the following eth0 filter to do both: host <remote IPsec peer IP>
The result should be some UDP 500 ISAKMP traffic and encrypted IPsec traffic on UDP 4500 or ESP Protocol 50 (NAT-Traversal or Native IPsec, respectively).
When troubleshooting, we recommend setting up a continuous ping down the tunnel with a larger-than-default size specified so that you can be sure the packets you are watching are your pings. To do this you can use the -l argument on Windows and the -s argument on Linux.
Updated on 24 Apr 2020
