Authentication
OIDC Authentication
VNS3 Licensing
Access Management
Clientpack Generation
Installing HTTPS
Firewall 2.0
Firewall
AWS Specific features
Firewall FWSets
VNS3 Variables
VNS3 Router
IPsec Configuration
IPsec Parameters
VNS3 Peering Mesh
Setting Topology Name
VNS3 Overlay Network
Snapshot Management
VNS3 Event Alerting
Network Address Translation
Traffic inspection
SNMP Support
VNS3 BGP Configuration Guide
Remote Support
Resetting VNS3
Upgrading
VNS3 Release Notes
VNS3 EOL Policy and Milestones
IPSec Connection Checklist
VNS3 Known Issues
VNS3 Specifications
VNS3 VPN Client tools
VNS3 Control Center
VNS3 setupIPsec Parameters
Cryptographic Parameters
VNS3’s IPSec subsystem is good at autodiscovery on IKE and ESP choices with a wide range of boxes. We recommend being as specific as possible when entering tunnel parameters. Match the algorithm, hash and DiffieH group for your gateway settings by specifying them in the “Extra Configuration” text field.
We support the following:
- combinations algorithms 3DES, AES128, AES256, (IKEv2 only: aes128_gcm, aes256_gcm)
- hashes SHA1, MD5, SHA2_256, SHA2_384, or SHA2_512;
- and DH groups 2, 5, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, (IKEv2 only: DH31).
Example entries for IKE (Phase 1) and ESP (Phase 2) in the extra params box:
phase1=aes256-sha2_512-dh14
phase1=aes256-sha2_256-dh14
phase1=aes128-sha1-dh5
phase1=3des-md5-dh2
phase2=aes256-sha2_512
phase2=aes128-sha1
phase2=3des-sha1
PFS Group Extra params entry for PFS Group is technically required only when it must be different from pfs group in phase1. If that is the case, then use:
pfsgroup=dh5
pfsgroup=dh14
pfsgroup=dh24
IKE and ESP Lifetimes
phase1-lifetime=3600s (default setting on VNS3)
phase2-lifetime=28800s (default setting on VNS3)
Dead Peer Detection - Disabled by default, to enable DPD to attempt to re-connect during periods of no response use the following:
dpdaction=restart (other options are “hold” meaning just wait, or “clear” meaning drop the security association)
dpddelay=30s
dpdtimeout=90s
Other, less frequently used options available are:
connection=bidirectional (default). Can also be “receive”, meaning to not initiate connections, only receive them.
connection-rekey=yes (default). Can also be “no” meaning no Phase1 or Phase2 re-key operations are done.
local-peer-id=<an address, a fully qualified domain name, a simple text string with no special characters> VNS3 default to Local Private IP for this value, it is common to set local-peer-id=
mtu=<an integer> - MTU stands for “maximum transmission unit”
For policy-based VPNs this is usually not specifically set. For route-based VPNs, if the connection is NOT going over the Internet but via a VPC/VNET peering link or a Direct Connect that supports “Jumbo Frames”, then “mtu” might be used to increase the size of the MTU (allowing higher throughput).
compat:some-text - This option should only be used at the instruction of Cohesive. It allows underlying parameters of the IPSec, BGP, Routing, Firewall, or SSL VPN subsystems to be passed straight into the environment with no parsing or validation. It is only used in a small fraction of interoperability situations.
Phase 1 Parameters
- Allowed Algorithms: 3des, aes128, aes256 (IKEv2 ONLY: aes128_gcm, aes256_gcm)
- Allowed Hashings: md5, sha1, sha2_256, sha2_384, sha2_512
- Allowed DH Groups: 2, 5, 14, 15, 16, 17, 18, 19, 20, 21, 23, 24
- Phase 1 Combinations
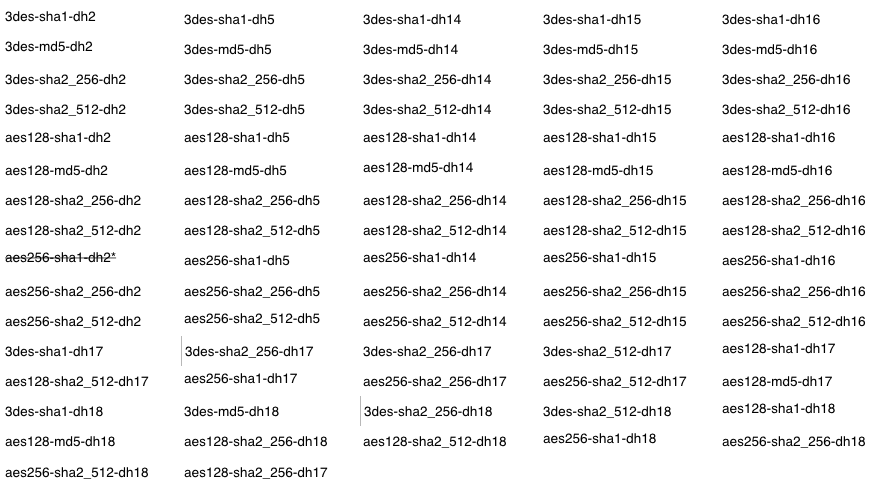
Phase 2 Parameters
- Allowed Algorithms: 3des, aes128, aes256, aes128_gcm, aes256_gcm
- Allowed Hashings: md5, sha1, sha2_256, sha2_384, sha2_512
- Perfect Forward Secrecy (PFS) DH Groups: 2, 5, 14, 15, 16, 17, 18 (IKEv2 only: 19, 20, 21, 23, 24, 31)
- Phase 2 Combinations:
- 3des-sha1
- 3des-md5
- 3des-sha2_256
- 3des-sha2_512
- aes128-sha1
- aes128-md5
- aes128-sha2_256
- aes128-sha2_512
- aes256-sha1
- aes256-md5
- aes256-sha2_256
- aes256-sha2_512
- aes128_gcm (Phase 2 does NOT have a hash/integrity function setting such as sha1, sha2_256, etc.)
- aes256_gcm (Phase 2 does NOT have a hash/integrity function setting such as sha1, sha2_256, etc.)
Updated on 24 Apr 2020
