VNS3:ms Overview
VNS3:ms Setup
Monitoring Cloud
Monitoring VNS3
VNS3:ms MFA
VNS3 Firewalls
High Availability (HA)
Triggering HA Events
VNS3 Controller Passwords
Managing Snapshots
User Administration
General Settings
VNS3:ms Backup
Installing SSL
Auditing
Remote support
Release Notes
VNS3:ms EOL Policy and Milestones
Installing SSL
SSL Certificates
Before adding a custom SSL certificate to a VNS3:ms instance, Cohesive Networks strongly recommends creating and downloading a DB Backup from the System Administration>Backup page. This backup can be used to re-instantiate the VNS3:ms system in the event the certificate/key pair creates an error (usually due to a mismatch or wrong files specified).
If you are unsure about the SSL Certificate files to upload, contact Cohesive Networks support staff to review. Very simply stated, SSL Certificates for HTTPS interactions provide web users website ownership verification (so users can make sure they are interacting with an organization they intend) and encryption of communication to that website.
In order to be granted an SSL Certificate, a site owner needs to create a private key file (use later in the interactions between the web browser and the actual web server). This private key file is then used to generate a Certificate Signing Request (CSR) that is sent to a Certificate Authority (CA) like Verisign or Geotrust.
The Certificate Authority then sends back the SSL Certificate which includes information about the owner of the certificate, period of validity, URL that is certified and the ID of the CA, the public key used for encrypting communications and a hash to ensure the certificate is valid and not compromised.
The SSL Certificate along with the Private key used to generate the CSR are the two files required to add the Certificate to a VNS3 instance.The next page reviews the relevant items and how to upload the SSL Certificate to VNS3.
To order an SSL Certificate from a Certificate Authority you need to validate you are the owner of the specific URL you are certifying (typically via email validation or similar depending on the CA) and generate a CSR to send to the CA. The CA then uses the CSR to create the SSL Certificate.
Generating a CSR
To generate a CSR you first must create a Private Key. This document’s example uses openssl. NOTE: VNS3 requires the private key to be an RSA key.
openssl genrsa -out vns3-example-com.key 2048
Once the private key is created, use it to generate the CSR with the following:
openssl req -new -sha256 -key vns3-example-com.key -out vns3-example-com.csr
The CA will send back one or multiple Certificates:
- Root Certificate - typically not needed for VNS3
- Intermediate Certificate - included if the CA is not a Root CA
- End User Certificate - the certificate for the actual URL you plan on secure
Installing SSL
Upload the SSL Cert or SSL Certificate Chain in the event your CA provided an intermediate Certificate (see example to the right) under the SSL Certificate file selection. General begins with “—–BEGIN CERTIFICATE—–”.
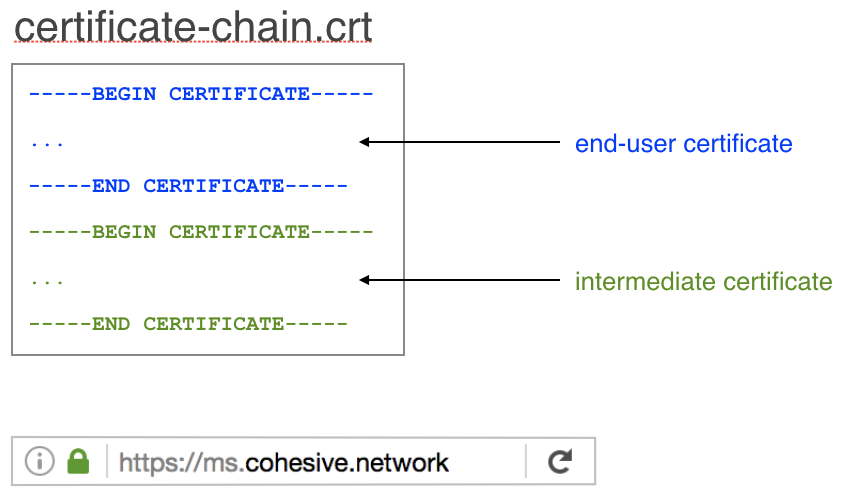
Then upload the Private RSA key file used to generate the CSR under the SSL Key file section. Generally begins with “—–BEGIN RSA PRIVATE KEY—–”.
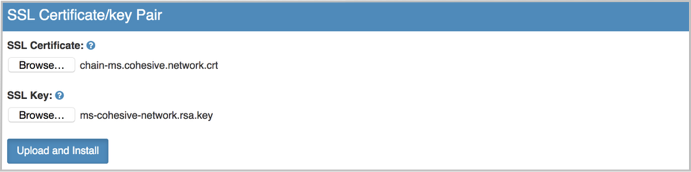
Click Upload and Install.
Updated on 13 Aug 2019
